Cyber security training at Hacker School equips students with a career that demands swift and strategic thinking to prevent data breaches and secure networks from unauthorized access. This field constantly changes with offensive and defensive moves, much like a dynamic chess game. The cyber security training provides the essential knowledge and abilities they need to […]
Category Archives: Hacker’s Blog
Best Online cybersecurity course in Hyderabad
The best online cybersecurity course in Hyderabad is offered by Hacker School. Learn ethical hacking, threat analysis, and advanced security techniques from industry experts. Gain practical skills and certifications to excel in your cybersecurity career. In today’s digital age, cyber security is essential as businesses rely on technology to store critical data, increasing cyber threat […]
Web Application Penetration Testing Training Institute in Hyderabad
Web Application Penetration Testing Training Institute in Hyderabad provides expert-led courses, offering hands-on labs and real-world techniques to master web app security and identify vulnerabilities effectively. A Detailed Overview of Web Application Penetration Testing Penetration testing for web applications is crucial for validating the effectiveness of security measures within an app. It plays a vital […]
Web application penetration testing course in Hyderabad
Web application penetration testing guide for beginners to experts. Hacker School provides comprehensive training in web app penetration testing to assist testing professionals in acquiring the skills needed to identify bugs and vulnerabilities in websites and web applications. The hands-on training sessions encompass a wide range of topics, including understanding how hackers discover weaknesses, executing […]
Web application penetration testing course in Bangalore
Hacker School teaches a thorough course on testing web applications to help professionals gain the skills needed to find and fix issues in websites and web apps. The practical training covers various aspects, such as understanding how hackers find weaknesses, carrying out attacks, defending against them, and reporting issues to developers. The Web Application Penetration […]
Cyber Security Training Institute in Hyderabad
With the increase in cybercrime and the clever tricks used by hackers, there’s a big need for cybersecurity experts who know how to use the latest tools and methods. To protect a company’s important information from being stolen, leaked, or attacked online, you need the right software and skilled cybersecurity staff. If you want to […]
How I made my terminal fun and handy
“Shell” if you are a Linux user, chances that you are not aware of the “shell” are slim. In case you dont know…
How I made my terminal fun and handy
“Shell” if you are a Linux user, chances that you are not aware of the “shell” are slim. In case you dont know…
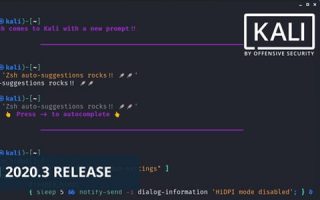
Kali 2020, What’s good and what’s Not?
When OffSec Released 2020 versions of Kali I was pretty much excited about it, but once released and when i started using it,.
Comparing Government Servers with Corporate Servers
When OffSec Released 2020 versions of Kali I was pretty much excited about it, but once released and when i started using it,..
Critical Vulnerabilities found in Zoom and Microsoft Teams
Amidst the current corona virus pandemic which has hit economies of all countries globally, security researchers…
Threats and Security Measures for IoT
These days everyone is interested in operating things remotely without being in contact with them and many times…
How to prevent Ransomware Attacks
One fine day my colleague received a mail that seems to be from his manager, he opened the mail. It contains some…
Initial Steps into Cyber Security Career
Are you interested in Ethical Hacking? Are you worried about your privacy and security in the digital space? Are you planning…
Creating Safe Hacking Environment
This blog article will help you in setting up a safe virtual environment for practicing ethical hacking skills…
Spreading faster than CORONA
If you are aware and concerned about the new pandemic CoronaVirus aka COVID-19, beware you can be a potential victim…
Problems with Smart Phones
In today’s world, a smartphone became a very integral part of human activities, calls, events, map guides, content…
Breach of TRUST
Ever since spectre and meltdown vulnerabilities arose, intel chipsets are facing constant mocking and developed…